ASEAN algorithm security is becoming increasingly crucial as the region embraces digital transformation. With the rise of AI and machine learning, protecting algorithms from vulnerabilities and malicious attacks is essential for maintaining trust and stability in the region’s digital economy. This necessitates a collaborative approach, involving governments, businesses, and individuals, to ensure a secure and prosperous digital future for ASEAN.
Understanding the Importance of Algorithm Security in ASEAN
The ASEAN region is experiencing rapid technological advancements, with algorithms playing a central role in various sectors, from finance and healthcare to transportation and e-commerce. This dependence on algorithms underscores the importance of robust security measures. A breach in algorithm security can have far-reaching consequences, impacting not only individual users but also businesses and even national security. Imagine a scenario where a malicious actor manipulates an algorithm controlling traffic flow in a major ASEAN city. The resulting chaos could have devastating consequences. The protection of algorithms, therefore, is paramount for ensuring the continued growth and stability of the region’s digital landscape. This involves understanding potential vulnerabilities, developing robust security protocols, and fostering a culture of cybersecurity awareness.
After the opening paragraph, here’s a link to learn more about ASE tracking application.
Threats to ASEAN Algorithm Security
Several factors contribute to the vulnerability of algorithms in the ASEAN region. These include:
- Data breaches: The increasing reliance on data makes algorithms susceptible to data breaches, which can compromise their integrity and accuracy.
- Adversarial attacks: Malicious actors can manipulate algorithms by feeding them carefully crafted inputs designed to trigger unintended behavior.
- Lack of awareness: A lack of cybersecurity awareness among developers and users can exacerbate vulnerabilities.
- Insider threats: Malicious insiders can exploit their access to algorithms to cause significant damage.
Protecting Algorithms in the Digital Age
Protecting algorithms requires a multi-faceted approach. This involves:
- Developing secure coding practices: Developers must prioritize security considerations throughout the software development lifecycle.
- Implementing robust access control mechanisms: Restricting access to sensitive algorithms can help prevent unauthorized modifications.
- Regularly auditing algorithms: Periodic audits can identify vulnerabilities and weaknesses before they can be exploited.
- Promoting cybersecurity awareness: Educating users about potential threats and best practices can empower them to protect themselves.
“In the interconnected world of ASEAN, algorithm security is no longer a technical issue; it’s a matter of regional stability,” says Dr. Anya Sharma, Cybersecurity Expert at the ASEAN Cyber Institute.
Building a Secure Digital Future for ASEAN
ASEAN can take proactive steps to build a secure digital future by:
- Fostering regional cooperation: Sharing best practices and coordinating responses to cyber threats can strengthen the region’s collective security posture.
- Investing in cybersecurity research and development: Supporting research and development in algorithm security can lead to innovative solutions.
- Developing a skilled cybersecurity workforce: Training and equipping cybersecurity professionals is essential for effectively addressing the growing threat landscape.
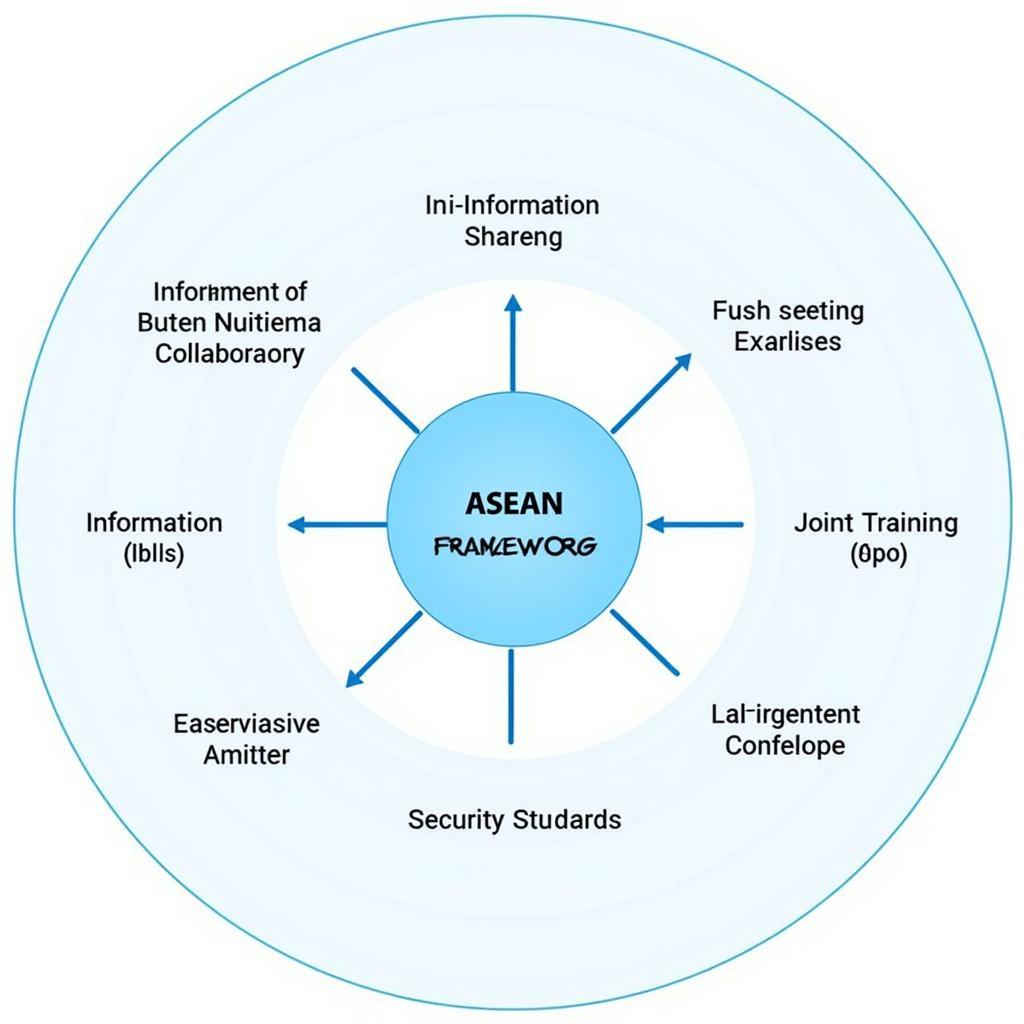 ASEAN Cybersecurity Collaboration Framework
ASEAN Cybersecurity Collaboration Framework
“The future of ASEAN’s digital economy depends on our ability to secure the algorithms that drive it,” emphasizes Mr. Kenji Tanaka, Chief Technology Officer at a leading ASEAN technology firm.
The Role of Individuals in Algorithm Security
Individuals also have a crucial role to play in ensuring algorithm security. This includes:
- Being aware of potential threats: Understanding how algorithms can be manipulated can help individuals identify and report suspicious activity.
- Practicing good cyber hygiene: Simple steps like using strong passwords and avoiding phishing scams can significantly reduce the risk of compromise.
- Staying informed about the latest security updates: Keeping software and devices up-to-date can patch vulnerabilities and protect against known threats.
You can find information regarding ASE fire panel here.
Conclusion
ASEAN algorithm security is a shared responsibility that requires a concerted effort from all stakeholders. By prioritizing algorithm security, ASEAN can foster trust in its digital ecosystem, protect its citizens, and unlock the full potential of its digital economy. Investing in research, promoting collaboration, and fostering a culture of cybersecurity awareness are crucial steps towards achieving this goal.
FAQ
- What is algorithm security?
- Why is algorithm security important for ASEAN?
- What are the main threats to algorithm security?
- How can ASEAN strengthen its algorithm security posture?
- What is the role of individuals in ensuring algorithm security?
- What are some examples of best practices for algorithm security?
- Where can I find more information about ASEAN algorithm security?
Learn about ASE credit card number.
ASE DS-9C might also be of interest.
ASE Deca Technologies is another related topic.
When you need support, please contact us at Phone Number: 0369020373, Email: aseanmediadirectory@gmail.com or visit us at: Thôn Ngọc Liễn, Hiệp Hòa, Bắc Giang, Việt Nam. We have a 24/7 customer support team.